Cover Photo generated with AI - 19th November 2023 at 17:59 UTC by DALL-E 3 via Bing Chat
Introduction
In this post, I’m going to talk about a problem I recently experienced with permissions in GitHub, how I worked around them and what you need to know about OAuth permissions in GitHub.
What happened?
I setup a brand new GitHub Organisation recently as part of a new side project of mine, so that I could keep all repositories for that project together and also separate from my default organisation for my user account.
I also set up 2 repositories in the new org, and set my user account as an Owner of the new org (therefore having full admin rights):
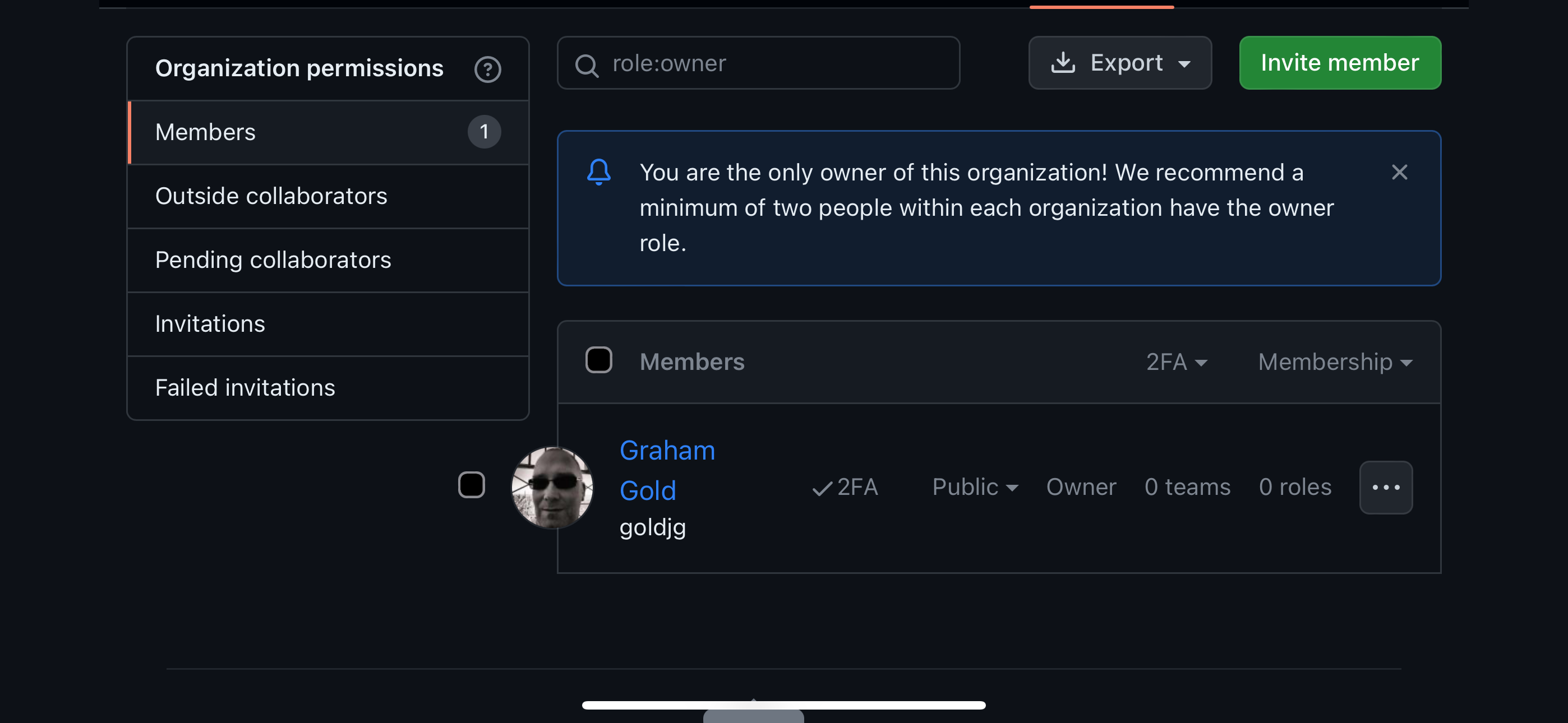
All good, right?
I then cloned the repositories into the Working Copy app that I use on my iPhone and iPad for managing my git repos.
I use an SSH key generated in the app, and the public key is uploaded to GitHub.
The clone of the repos was successful, but any attempt to push commits to them failed with the error below:
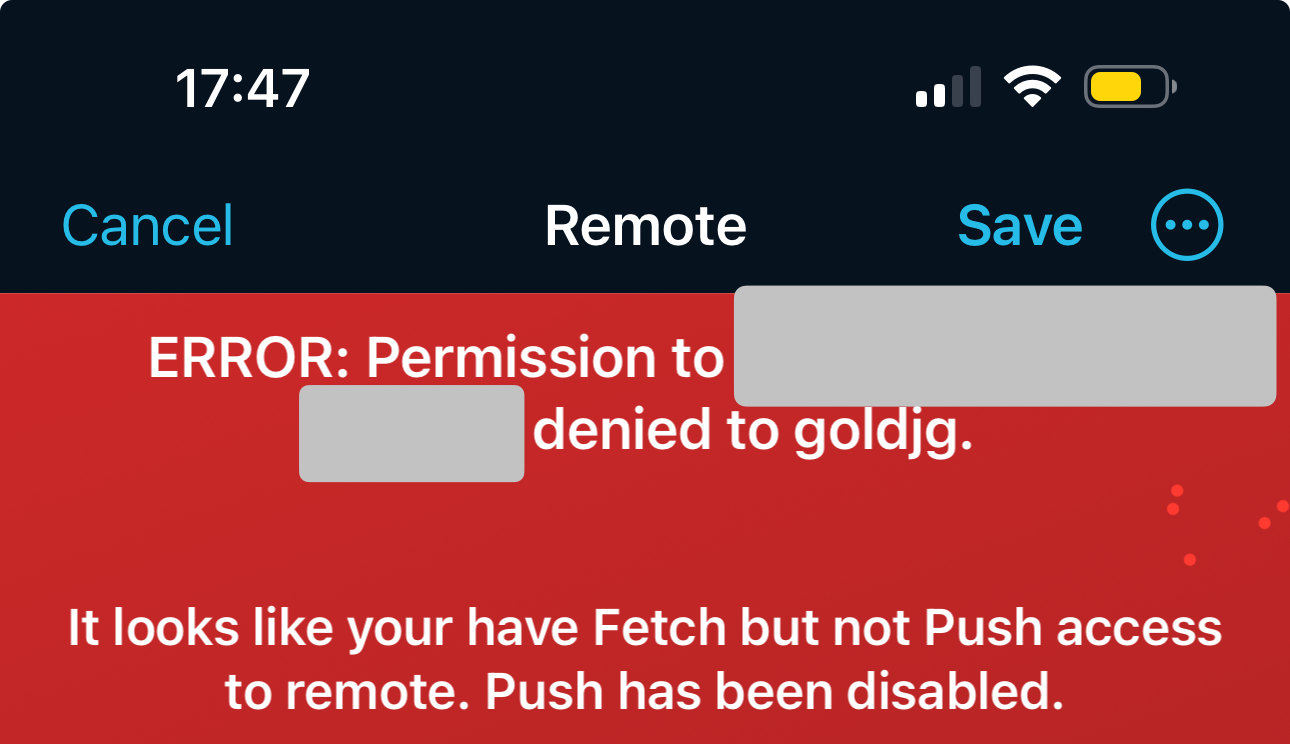
But I’m Owner and Admin so what gives?
OAuth App Access Restrictions
GitHub has a feature called OAuth App Access Restrictions which is enabled by default.
You can find these in the Settings for the organisation under Third-party application access policy:
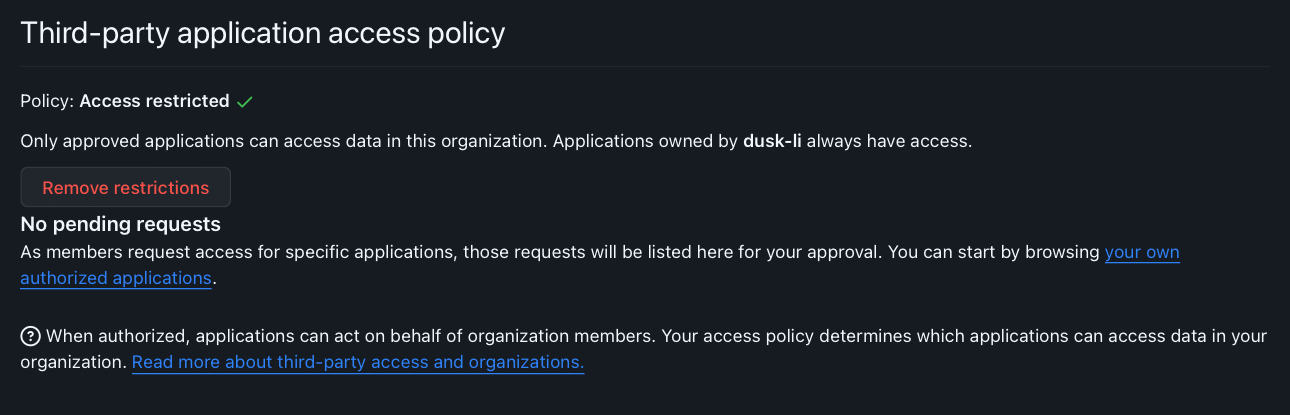
What those restrictions do is prevent write access to OAuth Apps (Working Copy, Azure DevOps etc) that have been authorised by a member of the organisation where they have not been authorised for the organisation.
It’s actually a really good security feature, and especially good that it is on by default.
You can read more about authorising OAuth applications here.
Disabling the policy
In my case, I own the org and will not be giving anyone else access at an Admin scope - I will let people submit PRs to the public repo but nobody can merge to the main branch except me or automated processes controlled by me.
So in this particular case, disabling the restrictions is a fairly low risk but please evaluate your own risk before disabling the policy completely!
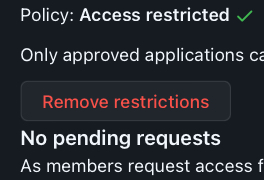
Go to Settings for the organisation under Third-party application access policy:

Click on Remove restrictions button:
You will see the following prompt:
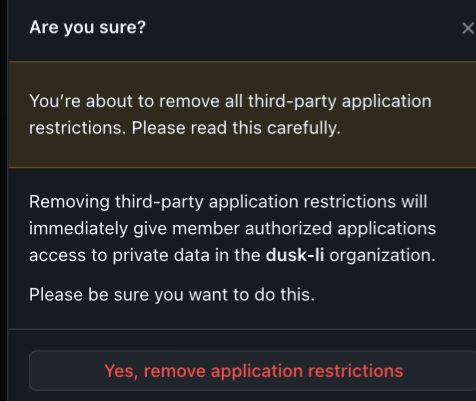
Click on Yes, remove application restrictions.
You should then see:
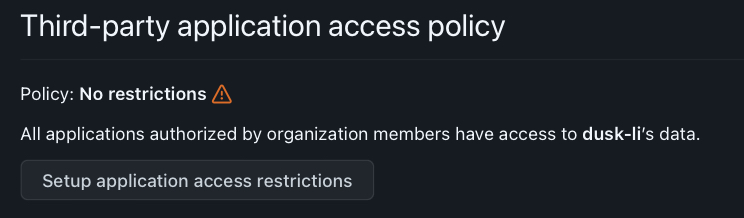
Once this is done you will be able to push to the repositories in your organisation.
Summary
To recap then, much as I tend to be quite critical of Microsoft on the security front, Third-party application access restrictions is a good security control, especially for organisations with multiple admins and privileged users, to reduce the risk of abuse of OAuth authentication flows.
If you are the sole owner and admin you may consider removing the restrictions as I did, but more likely you will want to go through the linked documentation to properly authorise applications that you trust to access your organisation.
As ever, thanks for reading and feel free to leave comments down below!
If you like what I do and appreciate the time and effort and expense that goes into my content you can always ![]()
