Image by Alexandre Debiève on Unsplash
Got a website?
Secured with HTTPS and an SSL certificate?
You’d know if someone tried to register their own certificate for your domain and masquerade as you, right?
If you answered Yes, Yes and No, and you’re using Cloudflare, you can fix that at the flick of a switch (well, click of a button!).
Read on to find out how…
Background
…IT security, is not a set it and forget it deal…
Millions of SSL certificates are now issued daily - which is a good thing!
However, SSL, like any other aspect of IT security, is not a set it and forget it deal - you have to constantly stay up to date with trends/exploits/vulnerabilities and ways to protect against them. Even then, one of the most important things you can do is to monitor the logs and metrics available to you - there’s no point having them if you don’t look at them after all.
…one of the most important things you can do is to monitor the logs and metrics available to you - there’s no point having them if you don’t look at them…
Now - we’re all busy - hence the push these days to automate all the things - there simply aren’t enough hours in the day otherwise.
And with SSL certificates, just having one isn’t enough - you also have to be on the lookout for bad actors (undesirables/malicious people, not your least favourite hollywood actor) that want to masquerade as you/your business and con your customers/rip off their data. One way of doing so is to get a certificate issued for your domain that they can use on their own nefarious website and pretend to be you/your site. Having a certificate that looks valid can add legitimacy to their site and also cause your own site not to function correctly.
Enter….Certificate Transparency
To quote LetsEncrypt:
Certificate Transparency (CT) is a system for logging and monitoring the issuance of TLS certificates. CT greatly enhances everyone’s ability to monitor and study certificate issuance, and these capabilities have led to numerous improvements to the CA ecosystem and Web security. As a result, CT is rapidly becoming critical infrastructure.
So what does that mean? Well, if you are monitoring CT logs, you’ll see any certificate being issued for your domain - knowing about it is the first step in being able to do something about it. This doesn’t help with monitoring for phishing attempts - monitoring CT-Logs for certificates issued for cirriustech.co.uk would not catch certificates issued for c1rriustech.co.uk or cirrius-tech.co.uk for example.
But even so, knowing that someone has managed to get a certificate issued for your domain is still worth knowing about - so how do we do that?
Well, as the title of the post suggests, if you are using Cloudflare to proxy your site, it is very simple indeed with a new feature they have in beta at present.
Enabling Certificate Transparency Monitoring on Cloudflare
Enabling this feature in Cloudflare is simple.
- Login to your cloudflare.com dashboard
- Select the domain you want to enable it for:
- Click on SSL/TLS

- Scroll down to Certificate Transparency Monitoring and click on the toggle to toggle it On
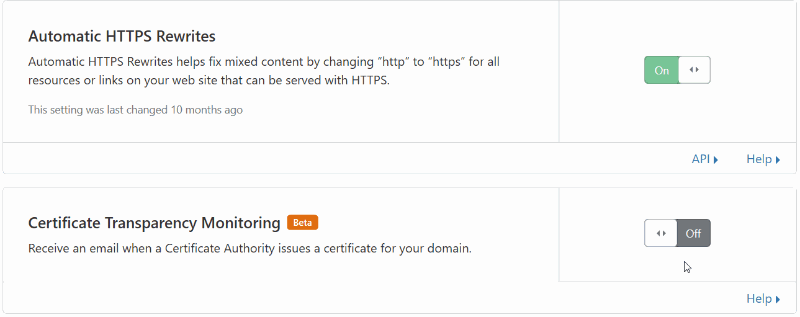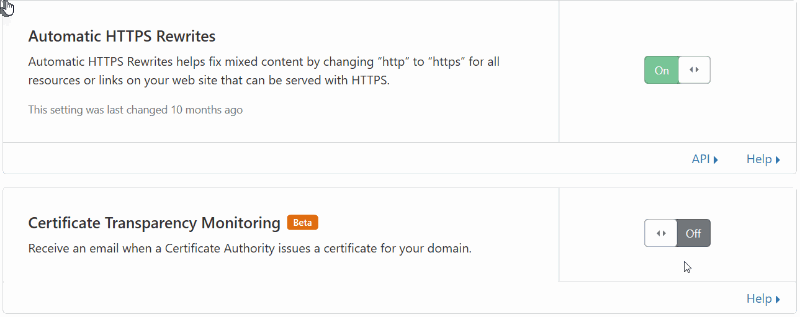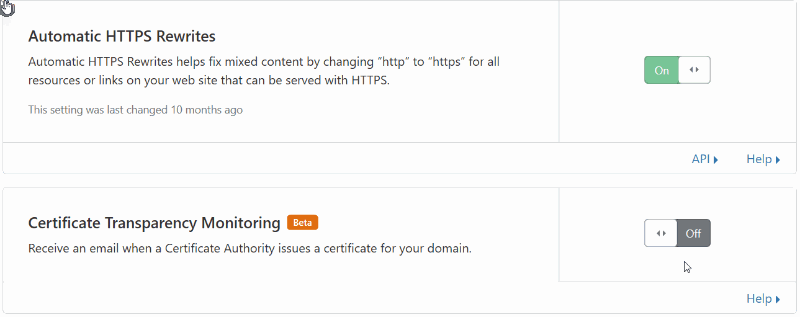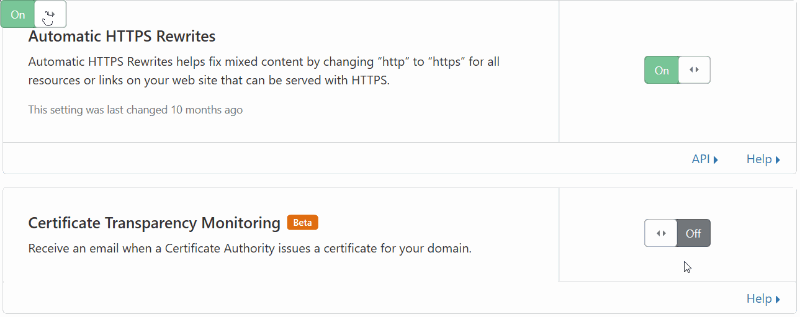
That’s it!
Now, if a certificate is issued for your domain, you’ll get an email notification from Cloudflare (to your registered address if you’re on Free or Pro account - or to specific addresses you register for this if you’re on Business or Enterprise).
What next?
If you were to get an email alerting that someone has in fact had a certificate issued for your domain (and you know it wasn’t you/legit), follow the advice on Cloudflare’s blog about the Certificate Transparency Monitoring feature.
Hopefully you’ll agree that this is a useful feature - and for next to no effort to enable it. It’s another tool in your toolbox to protect the security of your site, your users and your business.
As ever, thanks for reading and feel free to leave comments below.
If you like what I do and appreciate the time and effort and expense that goes into my content you can always ![]()
